IST,
IST,
Working Group report on Cloud computing option for Urban Cooperative Banks
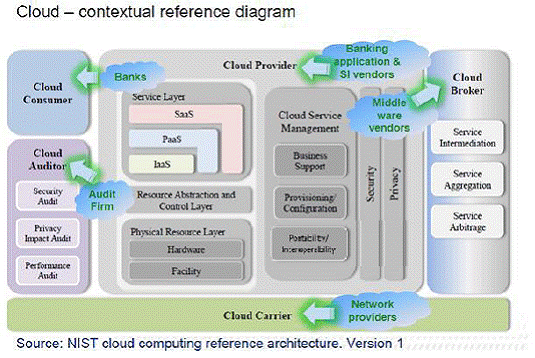
Working group for exploring use of Cloud Computing option for small size Urban Cooperative Banks was set up by RBI comprising senior officers from the Reserve Bank of India, experts from the software industry and eminent professors from academia. The working group reviewed the profile of the sector, technological trends in Cloud Computing and use of cloud like solutions within UCBs. Based on the analysis, the working group has suggested its approach for Cloud computing option. 2. RBI had already identified minimum IT support for front office and back office operations, MIS and Regulatory reporting. Though there has been a good progress particularly in banks having five and more branches which covered nearly 60% of the total banking business provided by the UCB sector, large number of banks having up to five branches still did not have core banking solutions. This segment of the sector is also characterised by absence of technical manpower, small size and low level of banking complexities. 3. The National Institute for Standards and Technology (NIST) has defined cloud computing as, "Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g. networks, servers, storage, applications and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. The NIST has proposed reference architecture for cloud computing wherein the IT services are provided as Infrastructure as Service (IaaS), Platform as service (PaaS) and software as a service (SaaS) with increasing level of abstraction for the cloud customer. It identifies the Cloud Provider, Cloud Consumer, Cloud Auditor, Cloud Broker and Cloud Carriers as the players in cloud computing and Private Cloud, Community Cloud, Hybrid Cloud and Public Cloud as deployment models with increasing level of service options but also increasing security concerns. The cloud model therefore is composed of five essential characteristics, three service models, and four deployment models. As target banks have limited technical skills and lack of or little software solutions, SaaS model could be suited for them. NIST has identified Open issues in cloud computing as Computing performance, Cloud reliability, Attainment of Economic goals, Compliance with regulations and Information security. The NIST has also identified Process and Technology oriented security concerns in cloud computing. The Information Systems Audit & Control Association (ISACA) has suggested six guiding principles, control objectives and framework as well as Audit scope for cloud environment. Chapter 1 1. Introduction: Compared to commercial banks, the size, scale of operations, skill set availability, preparedness for computerisation of Urban Cooperative banks are not high. Yet, there is need for computerisation by adoption of Core Banking Solution (CBS) by these banks to derive greater reach and provide better services. In order to understand the options available, DG(AS) had meetings with two of the prominent CBS providing firms. EDs and CGMs-in-charge of DIT and UBD also participated in the meetings. From the technology perspective following points emerged:
Depending on size and financial status, UCBs can adopt either CBS of their own or draw services from service provider. DG desired that an approach paper for adoption of CBS/Cloud services may be prepared by DIT. Accordingly, working group for exploring using Cloud Computing as option for small size Urban Cooperative Banks was set up with senior officers of DIT, UBD, DGBA, IT experts from the software industry and eminent Academicians in IT. The composition of the Group is as under:
2. Terms of Reference:
Chapter 2. 2.1 Methodology The working group adopted following methodology for the study:
Scope : The working group has looked only into the technology related aspects and has based its observations on the publically available information from the Standards setting organisations and the information obtained from the banks as well as software solution providers. Chapter 3. 3.1 The main recommendations of the Working Group on IT support to UCBs (Gandhi Committee) : Considering the concentration of small UCBs, the lack of uniformity in the levels of computerization and inadequate awareness about the efficacy of computers in enhancing competitiveness, the minimum IT infrastructure was identified as: a) Computerized front-end i.e. customer interface The working group had suggested Core Banking Solution (CBS) for adoption by the Urban banks. The models for acquiring the IT infrastructure were identified as i) Application Service Provider (ASP) Model in respect of the small banks. 3.2 Status of computerisation as on March 31, 2012
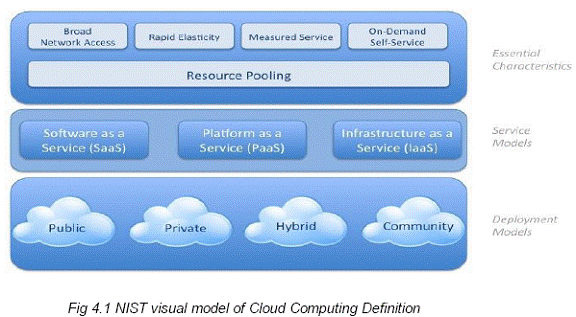
The Urban Cooperative banking sector is highly heterogeneous with concentration in a few states like Maharashtra and Gujarat. Further there are only limited numbers of banks who have sizeable share of total banking business done by the UCBs. In terms of availability of IT infrastructure as well as business profile, these large UCBs are similar to old generation private sector banks. The UBD study revealed that around 42% banks are unit banks and further 13% banks have only two branches. Nearly 80% banks have less than five branches. The solution is intended for these banks. Further, these banks have a limited banking services provided to their customers. In terms of technical as well as banking skills these banks are extremely limited. Many of these banks have either limited or no profit and have been facing financial stress. The Reserve Bank has taken many initiatives in this sector for consolidation as well as for strengthening the banks as a regulatory requirement. However, the cooperative credit structure has evolved as a means to meet the financing requirements of people of small means and has a history of over hundred years. They serve an important purpose of financial inclusion. The proximity to their customers and ability to understand their requirements of small and micro enterprises has been a unique feature and as a result these are viewed as instruments of extending banking services to people with small means. Further, the UCB sector is also characterised by its dual control as state governments have control over the governance structure through Registrar of Cooperative societies and RBI having say over the banking services provided by these banks. The technology solution to be proposed is expected to help these banks to improve efficiency of their transaction processing capabilities, housekeeping and customer service as a means to meet the competitive pressure on these banks. In other words, the solution to be provided needs to provide a level playing field to these banks in terms of access to IT solutions. Chapter 4: 4.1 Introduction to cloud Computing 4.1.1 Definition: Cloud Computing has become ubiquitous concept (term / idea) in Information Technology arena and is widely agreed to be the key to future of IT. National Institute of Standards and Technology (NIST) has defined cloud computing as: "Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.” As per NIST definition, cloud computing needs to satisfy five essential characteristics, use one of the three service models and deploy using one of the four models as depicted in the following diagram:
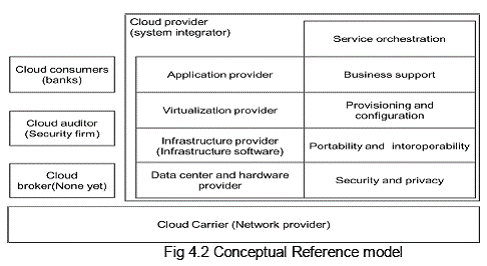
The five essential characteristic are (a) On demand self-service i.e. provisioning of additional computing facilities without human intervention (b) Broad network access i.e. accessibility from a variety of devices (c) Resource pooling i.e. sharing of infrastructure like data centre, hardware, infrastructure software and application software across banks (d) Rapid Elasticity i.e. resources allocated to a bank can grow or shrink dynamically depending upon load and (e) Measured service i.e. pricing would be based on actual usage rather than cost of equipment. Service models for would could be (a) Infrastructure as a Service (IaaS), which is typically used by IT managers / system administrators to commission additional machines on the cloud, typically to address temporary spikes in computing requirements (b) Platform as a Service (PaaS), where infrastructure on the cloud is used by application developers to develop applications and (c) Software as a Service (SaaS), where infrastructure on the cloud is used by end-users to use already developed applications. While all three models can be used by banks, “Software as a Service” which would be of relevance to cooperative banks considering that they have lean IT departments and model providers, higher level of abstraction which could help UCBs only on transaction processing while leaving details of HW, SW and Networking to the Service Provider. Deployment options could be (a) private cloud, where the entire infrastructure would be meant for a single bank (b) public cloud, where infrastructure would be available to general public (c) community cloud, where infrastructure would be used by a group with common interests and (d) hybrid cloud, which would leverage infrastructure on more than one of the above deployment models. While all the above deployment models can be used by banks, this report would concentrate on understanding the model presently being used in the banking industry, in this case, urban cooperative banks. Parties involved within various aspects of cloud deployment: Before we proceed further, we would like to depict roles and responsibilities of various parties involved in cloud deployment. This refers to conceptual reference model as described by NIST2.
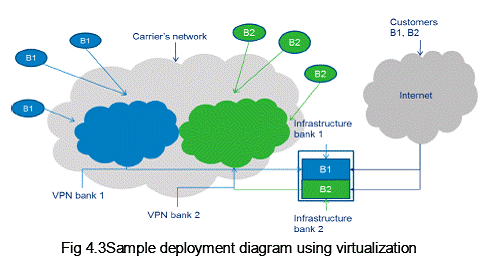
4.1.2 Essential characteristics: On-demand self-service: Cloud allows consumer to unilaterally provision IT infrastructure in the cloud in terms of computing resources, network capacity, storage requirements, etc., on demand basis. This means that cloud provider should be able to provide additional computing capacity without human intervention e.g. addition of new branches or addition of new customers or accounts. Broad network access: Cloud resources are accessible over the network through plethora of devices through standard mechanisms. Heterogeneous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations) can be used to access cloud. Resource pooling / Multi-tenancy: Cloud provider provides infrastructure, including data centre, air conditioning, power supply, hardware, infrastructure software, storage, and network which can be shared between different consumers. There can be a logical separation between each consumer’s computing resources and network using virtualization and VPNs or other techniques. Sample deployment diagram using virtualization is as shown in the figure below.
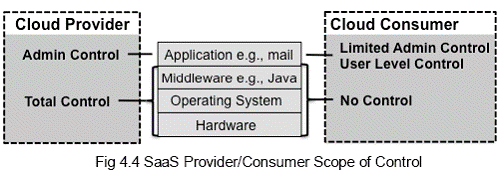
Rapid elasticity: Capabilities can be rapidly and elastically provisioned, in some cases automatically, to scale rapidly outward and inward commensurate with demand. In the context of bank customers, the capabilities available can be appropriated in any quantity at any time. Measured Service: Nature of Cloud service makes it possible to measure the usage of services/resources like storage, processing, bandwidth and active user accounts. Resource usage should be monitored, controlled, and reported; providing transparency for both the provider and consumer of the utilized service. In the context of banks, the Cloud provider should have reporting mechanism while billing. 4.1.3 Service Models: Cloud Software as a Service (SaaS): The capability provided to the consumer is to use the provider’s applications running on a cloud infrastructure. The applications are accessible from various client devices through a thin client interface such as a Web browser (e.g., Web-based email), or a program interface. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage, or even individual application capabilities, with the possible exception of limited user-specific application configuration settings. Basically consumers are organizations and application providers for end users. Control: As for the scope of control, service providers control most of the resources on the cloud and consumer has limited control of application related resources only.
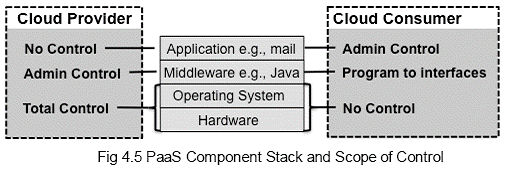
Benefits: The key benefits of SaaS clouds are: very modest software tool footprint, efficient use of software licenses, centralized management and data, platform responsibilities managed by providers, and savings in up-front Costs. Issues: But there are issues and concerns such as browser-based risks, network dependence, lack of Portability between SaaS, and isolation vs. efficiency (Security vs. Cost Tradeoffs) Candidate applications: This model is useful for business logic (CBS, Customer Relationship Management, Inventory Management, Fund transfer), Collaboration (Email, Portal, etc.), Office Productivity (Word processors, spread sheet, presentations programs, etc), Software tools (Security scanning and analysis, compliance checking, etc). Cloud Platform as a Service (PaaS): The capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created or -acquired applications created using programming languages and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, or storage, but has control over the deployed applications and possibly application hosting environment configurations. Here consumers are application developers, application testers, application deployers, application administrators, and application end users (Saas) Control: As for the scope of control, service providers control most of the resources on the lower layer but less than as compared to SaaS cloud. Consumer enjoys slightly more control on application as well as middleware.
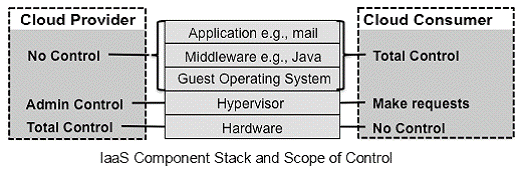
Benefits: PaaS clouds shares same benefits as SaaS namely very modest software tool footprint, efficient use of software licenses, centralized management and data, platform responsibilities managed by providers, and savings in up-front Costs. Apart from that it allows consumer a low cost option to develop and deploy the application on the cloud. This also helps to an extent overcome issue of lack of portability between service providers as consumer has control over application and data. Issues: PaaS cloud has same issues as SaaS such as browser-based risks, network dependence, and isolation vs. efficiency (Security vs. Cost Tradeoffs). Apart from that portability across PaaS platform, have to provision more resources to honour time bound request and consumer has to maintain IT expertise to take care of application. In case it is provided by third party, then one more layer of complexity is added in service provider management for the consumer. Candidate applications: This PaaS model is useful same set of applications as for SaaS viz. business logic (CBS, Customer Relationship Management, Inventory Management, Fund transfer), Collaboration (Email, Portal, etc.), Office Productivity (Word processors, spread sheet, presentations programs, etc), Software tools (Security scanning and analysis, compliance checking, etc). Cloud Infrastructure as a Service (IaaS): The capability provided to the consumer is to provision processing, storage, networks, and other fundamental computing resources where the consumer is able to deploy and run arbitrary software, which can include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, deployed applications; and possibly limited control of select networking components (e.g., host firewalls). The consumer here is system administrators. Control: As for the scope of control, service providers control most privileged lowest layer but less than as compared to PaaS cloud. Consumer enjoys much more control on application, middleware and OS.
Benefits: IaaS clouds provide benefits in terms of savings in up-front Costs, allows full control of IT resources, flexible and efficient renting of resources, and its resolve the problems of portability and interoperability. Issues: IaaS cloud has issues such as browser-based risks, network dependence, legacy application security issue, VM security issue in terms of missing security update, robustness of VM isolation, and data erase practices. Candidate applications: This IaaS model is useful for system integrators or other service providers to develop test and deploy applications for end users/ organizations. 4.1.4 Deployment Models: Private cloud: The cloud infrastructure is provisioned for exclusive use by a single organization comprising multiple consumers (e.g., business units). It may be owned, managed, and operated by the organization, a third party, or some combination of them, and it may exist on or off premises. Community cloud: The cloud infrastructure is provisioned for exclusive use by a specific community of consumers from organizations that have shared concerns (e.g., mission, security requirements, policy, and compliance considerations). It may be owned, managed, and operated by one or more of the organizations in the community, a third party, or some combination of them, and it may exist on or off premises. Public cloud: The cloud infrastructure is provisioned for open use by the general public. It may be owned, managed, and operated by a business, academic, or government organization, or some combination of them. It exists on the premises of the cloud provider. Hybrid cloud: The cloud infrastructure is a composition of two or more distinct cloud infrastructures (private, community, or public) that remain unique entities, but are bound together by standardized or proprietary technology that enables data and application portability (e.g., cloud bursting for load balancing between clouds)." 4.2 Reference Architecture for Cloud Computing
Fig 4.7 Cloud computing reference architecture There are fundamental technical building blocks for cloud computing viz. • SOA—A library of proven, functional software applets that can be connected to become a useful application • Application programming interfaces (APIs)—Tags to direct applets about the Internet • XML—Identifier tags attached to information (data, pages, pictures, files, fields, etc.) that allow them to be transported to any designated application located on the Internet 4.3 Open issues in cloud computing Cloud services helps consumer to outsource the maintenance burden of servers and applications; scale systems up or down on demand; being able to access data from anywhere with a network connection; and the ability to replace occasional heavy capital expenditure (CAPEX) on IT with regular and predictable operational expenditure (OPEX). From a provider's perspective, cloud computing allows capital expenses to be leveraged into positive revenue streams after initial investments are made. Cloud computing is evolving technology and will contain flaws, experience failures, and experience security compromises. Different service aspects of Cloud are yet to be standardized like end-to-end security, Portability, Interoperability, Service level agreement, etc. There are some issues which are unique to it and some already exists. There are challenges in adopting Cloud computing as can be seen from open issues such as Computing performance, Cloud reliability, Economic goals, compliance, and Information security, which are discussed below : 4.3.1 Computing Performance Like any other form of computing on network, cloud computing face performance issue in terms of time take to process request over network, data synchronization, scalability of application and data management. Latency is the time taken to process the application request over the network (round trip). Multiple components and hops are involved starting from the end user desktop (Interface card) to LAN, end user router, network cloud, perimeter of provider, LAN and ultimately the application. Clear cut demarcation and responsibility, network optimization tools, web acceleration technologies and application capabilities to an extent can assure certain level of acceptable performance. Off-line Data Synchronization is critical for any network based application to take care of outages at network or consumer level. Technology adopted should be capable of taking care of version control and re-sync data. Scalable programming to leverage the scalable computing and network resources will be needed. Applications need to be re-engineered to realize the full benefits of the new computing capacity, which will be available on demand. Data storage management becomes critical issue as data, especially finance related, will be residing in the provider’s cloud. Consumer should be able to scale data storage on demand basis, restrict physical location of the data at rest (database, tapes, etc) to handle issue of data sovereignty, ensure proper process for data purging and disposing of data storage hardware and administer access control over the data. 4.3.2 Cloud reliability Reliability refers to the probability that a system will offer failure-free service for a specified period of time within the bounds of a specified environment. This issue is more acute as services are availed from the cloud and are residing on provider’s premises. Since cloud consists of multiple components, measuring reliability of individual component may be easier but difficult when taken together. Each component has specific reliability in given context and when all components taken together with their inter-dependencies, it will throw up more complications. The issue of reliability of the cloud depends upon the: Cloud provider outages (hardware, software and personnel’s), connectivity to the subscribed services, and the consumer’s personnel. The provider’s infrastructure {HVAC, IT components (hardware, software, network, security, etc.,) personnel’s, physical security, etc.} is prone to outages due to hardware, software or man-made issues. The SLA should clearly reflect uptime and performance parameters and alternatives for contingency situations. Network becomes critical component for any cloud based applications. It poses questions of availability on continuous basis, security risk for critical data in transmission, vulnerability to virus/worms/DOS attacks to name a few, physical cables cutting, natural disasters, etc. Network outages have to considered and contingency planning to be done for such events.4.3.3 Economic goals Cloud computing offers benefits to consumers in terms of converting their capex to opex and improve business agility by deploying and testing application and reaching to market in no time. But such benefits come with varied risks like risk of business continuity, SLA risk, portability and interoperability issues and disaster recovery. Risk of business continuity is clearly visible where on-site resources can be run even if vendors have withdrawn or suspended the services. But in case of cloud, consumers are completely dependent upon service providers for running their IT services. In case of banks running their financial application like CBS, service provider suspension will bring complete halt to their whole business of banking. Service Agreement is another area where consumers has to ensure that all aspects of cloud services are taken care of in terms of performance, outages, penalty, disaster recovery, portability, exit provision and data security, to name a few. Lack of standardization of SLA as well as difficulty in quantifying and measuring the terms of contract pose a greater risk to cloud consumer (UCBs). Portability and Interoperability are related issues on cloud computing. Interoperability is like the successful communication between, or among systems, and portability is ability to use components or systems in multiple hardware or software environments. As for the portability, consumer should be able to migrate from existing system to cloud or from one service provider to another or back to the consumer from cloud with least effort. Such portability demands standardisation at various interface level – network, application, middleware, etc. as well as at data format level. As for the interoperability consumer should be able to use other service providers cloud like during ‘Cloud bursting’ or a situation where cloud services of the provider are severely stressed. Disaster recovery becomes more critical in cloud environment as it will impact number of consumers hosted in the service provider’s cloud. Service provider should follow industry standard for DR site and setup, proper processes, and perform frequent DR drill. 4.3.4 Compliance Consumers availing the cloud services are accountable to different stakeholders like end customers, regulators and other bodies for compliance. In cloud computing, the lack of visibility, jurisdiction and regulation issue, actual location of data, and support for forensics plays a critical role in compliance. Consumer lacks visibility in cloud computing as how it operates and whether services are delivered in secured manner, end-to-end. Security event and information management at provider’s end with information sharing with consumer will help to reduce lack of visibility. Providers decide the physical cloud location on the basis of economic and other resources factors, whereas that may not meet the consumers compliance requirement like in case of data to be within national borders. Consumers have to adhere to variety of regulations as stipulated by the respective industry regulators. Consumers, who are ultimately responsible for their data processed on provider’s systems, will need to require assurances from providers that they are aiding in compliance of the appropriate regulations. This will require independent third party audit on regular interval basis to ensure that provider is meeting compliance requirements on continuous basis. Provider will have to agree for audit and investigative support and it can be made part of SLA. Consumers also need to know the legal jurisdiction and be able to get legal remedies for any failure on part of provider to meet contract terms. As nothing is full proof, some incident or event is bound to happen. To take care of such security events and incidents, digital forensics has to be carried out. It should clearly delineate the roles and responsibilities between provider and consumer. Also mutually agreed process should be in place for incident and security breach handling and management. 4.3.5 Information security Confidentiality and integrity of data with availability of data is the main crux of information security. Business critical information of consumer has to be monitored and protected at all level. As such, organizations employs various controls like Administrative controls for data operation, Physical control to protect storage media and facilities, and Technical control by employing Identity and Access Management, and by encrypting data in transit as well as at rest. In case of cloud, there are more complexity depending upon the way cloud is implemented, the attack surface of cloud, types of attackers, system complexity, expertise level of cloud administrators, to name a few. Data has to be protected during transit and at rest by encrypting with sufficient long key length and proper key management. Data privacy has to be maintained through legal and technical channel. More so; in multi-tenancy environment where multiple customers access, application and data resideing in same physical boxes. Access segregation, application segregation and more so data segregation has to be done using advance technology and clear cut process and guidelines to be laid down for the same. Privileged access to data has to monitored and controlled. Even consumers has to ensure that interface (thin or thick client) use by them to access the cloud services is secured, updated with latest patch and well protected.4.4 Saas model and issues in implementation Cloud Software as a Service (SaaS): SaaS as introduced in 4.1.3 prima facie seems to more suitable model for cloud computing especially for smaller banks. The applications are accessible from multiple devices. The consumer does not manage or control the underlying cloud infrastructure. Benefits: The key benefits of SaaS clouds are: very modest software tool footprint, efficient use of software licenses, centralized management and data, platform responsibilities managed by providers, and savings in up-front Costs. i) Very Modest Software Tool Footprint : As browsers that are capable of efficiently displaying interactive content have become ubiquitous, SaaS application deployment has become increasingly convenient and efficient with little or no client-side software required. Several factors contribute to this value proposition:
ii) Efficient Use of Software Licenses: License management overheads can be dramatically reduced using SaaS. Consumers can employ a single license on multiple computers at different times instead of purchasing extra licenses for separate computers that may not be used and thus over-provisioning the license. Additionally, traditional license management protocols and license servers are not needed to protect the intellectual property of application developers because the software runs in the provider's infrastructure and can be directly metered and billed. iii) Centralized Management and Data: The SaaS service model implies that the majority of the data managed by an application resides on the servers of the cloud provider. The provider may store this data in a decentralized manner for redundancy and reliability, but it is centralized from the point of view of consumers. This logical centralization of data has important implications for consumers. One implication is that, the SaaS provider can supply professional management of the data, including for example, compliance checking, security scanning, backup, and disaster recovery. When these services are provided away from the consumer's premises in public and outsourced scenarios, SaaS management of data gives consumers protection against the possibility of a single catastrophe destroying both the consumer's facility and data. This benefit, however, is contingent upon the SaaS provider protecting its facilities from catastrophic attack or other undesirable events. The “on demand” network access of SaaS applications also relieves consumers from the need to carry their data with them in some settings, thus potentially reducing risks from loss or theft. When supported by the application's logic, remote data management also facilitates sharing among other consumers. iv) Platform Responsibilities Managed by Providers: Generally, for outsourced or public SaaS clouds, consumers need not become involved with the management of a provider's infrastructure. For example, consumers need not be distracted by which operating system, hardware devices or configuration choices, or software library versions underlie a SaaS application. In particular, providers have responsibility for operational issues such as backups, system maintenance, security patches, power management, hardware refresh, physical plant security, etc. Providers also have an obligation to field services that guard against known exploits at the application level. Further, consumers are not required to maintain on premises IT support to perform these tasks, with an exception that on premises IT support is still necessary to connect consumer browsers securely to the network. Because SaaS providers implement new application features and provide the server side hardware that runs them, SaaS providers also have advantages in managing the introduction of new features while mitigating the need for consumers to upgrade their hardware systems to use the new features. v) Savings in Up-front Costs: Outsourced and public SaaS clouds allow a consumer to begin using an application without the up-front costs of equipment acquisition, but potentially with a recurring usage fee. Additionally, cloud providers should be able to provision their hardware, power, and other computing resources at scale and more efficiently than individual consumers, which may reduce ongoing costs to consumers. This provides a basis for cost savings to consumers. Issues and concerns: But there are issues and concerns such as browser-based risks, network dependence, lack of Portability between SaaS, and isolation vs. efficiency (Security vs. Cost Tradeoffs)i) Browser-based Risks and Risk Remediation: Although browsers encrypt their communications with cloud providers, subtle disclosures of information are still possible. For example, the very presence or absence of message traffic, or the sizes of messages sent, or the originating locations may leak information that is indirect but still of importance to some consumers. Additionally, even strong cryptography can be weakened by implementation mistakes; a common mistake is to generate keys or passwords in a manner that reduces their strength, thus making the cryptography vulnerable to brute-force guessing attacks. Furthermore, man-in-the-middle attacks on the cryptographic protocols used by browsers [Mar09] can allow an attacker to hijack a consumer's cloud resources. By relying on a consumer’s browser for software application interfaces, the SaaS approach also raises a risk that, if a consumer visits a malicious Web site and the browser becomes contaminated, subsequent access to a SaaS application might compromise the consumer's data. Another risk is that data from different SaaS applications might be inadvertently mixed on consumer systems within consumer Web browsers. One work-around to this issue is for consumers to use multiple browsers and to dedicate specific browsers to important SaaS applications and not to perform general-purpose Web surfing that may expose them to attack. Another work-around is for consumers to use a virtual desktop when connecting to cloud-hosted applications, which provides a secure, fully functional work platform that is governed by strict policies for limiting what can or cannot be accessed elsewhere, while connected to a cloud. ii) Network Dependence: The availability of a SaaS application depends on a reliable and continuously available network. In the public SaaS cloud scenario, the network's reliability cannot be guaranteed either by the cloud consumer or by the cloud provider because the Internet is not under the control of either one. In outsourced private or community SaaS scenarios, network security and reliability can be achieved using dedicated, protected communications links, but at a cost. Although a SaaS application may include a "disconnected mode" for continued processing during network outages, the fundamental organization of SaaS, with application logic implemented on the cloud provider's servers, implies that the actual functionality of the application will be dependent on its ability to access a reliable network. iii) Lack of Portability between SaaS Clouds: Portability in SaaS is a concern for transitioning workloads from one SaaS cloud to another. Formats for exporting and importing data may not be fully compatible among SaaS clouds. Customized workflow and business rules, user interface and application settings, support scripts, data extensions, and add-ons developed over time can also be provider specific and not easily transferable. iv) Isolation vs. Efficiency (Security vs. Cost Tradeoffs): There exist a trade-off between isolation and efficiency as well as security vs cost depending upon how application software is executed by a SaaS provider. Candidate applications: This model is useful for business logic, Collaboration, Office Productivity, and Software tools:
Recommendations: The following are additional recommendations for SaaS systems:
4.5 Security issues in cloud computing As discussed earlier, cloud computing is evolving technology and could be expected to contain flaws, experience failures, and security compromises. There are some issues which are unique to Cloud Computing. NIST has identified Process oriented and Technical oriented security features to rectify or mitigate the known security issues in cloud computing. 4.5.1 Process-oriented security requirements Process oriented security covers Security controls, Cloud Audit & assurance, log management, Cloud Certification and Accreditation, Cloud privacy guidelines, Clarity on cloud actors security roles & responsibilities, Trustworthiness of cloud operators, BCP and DR of cloud services, and Continuous Monitoring capabilities.
4.5.2 Technical-oriented security requirements Technical-oriented security requirements cover Visibility for consumers, Control for consumer, Data Security, Risk of Account Compromise, Identity Credentials and Access Monitoring and Authorization, Multi-Tenancy Risks and Concerns, Cloud based Denial of Service, and Incident Response.
4.6 Audit issues in cloud computing Audit plays much more critical role in cloud environment due to multiple consumers availing with critical and not-so critical service and solution and can have systemic wide implications, if consumers are from systemically important infrastructure services like finance and banking, power, etc. Audit can play more proactive role to ensure sustainability of cloud services with minimum outages and security breach. As a first step, enterprises need to clear about availing cloud services and solutions. The Information Systems Audit & Control Association (ISACA) has undertaken extensive research on Audit Assurance issues and IT Governance issues specific to Cloud Computing which are discussed below:4.6.1 ISACA Guiding principles for cloud computing ISACA has provided six guiding principles for cloud computing adoption and use. It has stated that it is too early in the life cycle of cloud computing to propose strict rules for the adoption and use of cloud infrastructures, platforms or software services. However; ISACA feels that principles that provide prudent boundaries of behaviour or describe a basic quality of trust or value applicable to cloud computing will help support decision making that will, in turn, reduce pressures and control risk. The six guiding principles for adopting and using the cloud are Enablement, Cost Benefit, Enterprise Risk, Capability, Accountability and Trust: 1. Enablement: To plan strategically for cloud adoption and use, enterprises need to:
2. Cost benefit: To properly evaluate the costs and benefits of cloud computing, enterprises need to:
3. Enterprise risk: To understand the risk implications of cloud computing, enterprises need to:
4. Capability: To leverage both internal and cloud provider resources effectively, enterprises need to:
5. Accountability: To ensure that responsibilities are clearly understood and individuals and groups can be held accountable, enterprises need to:
6. Trust: To ensure that business processes that depend on cloud computing can be trusted, enterprises need to:
4.6.2 Control objectives for cloud computing by ISACA Control objectives sets good practices for the ends, by providing enterprises with the structure they require to measure, monitor and optimise the realisation of business value from investment in IT / cloud. COBIT addresses IT / cloud risk and controls throughout an entire program life cycle. Reflecting actual program implementations, these risk controls are interrelated. the Control objectives framework included following four domains which in turn contain processor. • Plan and Organize (PO)— Provides direction to solution delivery (Acquire and Implement) and service delivery (Deliver and Support). Which are other two domains. • Monitor and Evaluate (ME)— Monitors all processes to ensure that the direction provided is followed. Effective IT performance management requires a monitoring process. This process includes defining relevant performance indicators, systematic and timely reporting of performance, and prompt acting upon deviations. Monitoring is needed to make sure that the right things are done and are in line with the set directions and policies. The COBIT framework is a generic framework for all IT infrastructure and as Cloud Computing emerged, the framework has been suitably adjusted to the features of Cloud computing. 4.6.3 Cloud governance - ISACA ISACA defines IT Governance as the set of responsibilities and practices exercised by the board and executive management with the goal of providing strategic direction, ensuring that objectives are achieved and ascertaining that risks are managed appropriately. The Cloud Computing is accelerating and mandating the transition and, therefore, Cloud Governance is necessary. When enterprises decide to utilize cloud services for some or all IT services, business processes are impacted, which makes governance more critical than ever. In such cases, enterprises should: • Effectively manage increasing risk, including security, compliance, projects and partners For enterprises to gain benefit from the use of cloud computing, a clear governance strategy and management plan needs to be developed. The strategy should set the direction and objectives for cloud computing within the enterprise, and the management plan should execute the achievement of the objectives. Enterprise governance of cloud projects requires acknowledgment of regulatory compliance requirements at both where the data are sourced and where the data are stored. New legal issues are already arising relative to the cloud. Detailed due diligence (know your provider, right to audit, assured continuity, security policy and process transparency), an understanding of expected cloud client responsibilities, and review and negotiation of candidate service provider SLAs and contracts are necessary while opting for Cloud Solutions. 4.6.4 Audit charter for Cloud environment - ISACA Objective and Scope of Audit Objective—The cloud computing audit/assurance review will: • Provide stakeholders with an assessment of the effectiveness of the cloud computing service provider’s internal controls and security The cloud computing audit/assurance review is not designed to replace or focus on audits that provide assurance of specific application processes and excludes assurance of an application’s functionality and suitability. Scope—The review will focus on: • The governance affecting cloud computing Minimum Audit Skills : As per ISACA guidelines, Cloud computing incorporates many IT processes. Since the focus is on information governance, IT management, network, data, contingency and encryption controls, the audit and assurance professionals should have the requisite knowledge of these issues. In addition, proficiency in risk assessment, information security components of IT architecture, risk management, and the threats and vulnerabilities of cloud computing and Internet-based data processing is also required. Implications for the proposed solution for UCB The review of available professional literature indicates that Cloud Computing is an emerging discipline in IT based services. The standards in various areas are still emerging and only a broad framework is suggested. The cloud model has different roles as cloud provider, cloud carrier, cloud consumer and the cloud auditor. The role of Cloud auditor is important for providing assurance on many issues. Although the skill sets at the end users could be lower, the knowledge and skills for designing, implementing as well as for evaluating and for auditing Cloud Computing environment are complex and demanding. Chapter 5 Two major Software solution providers have provided their core banking solutions to UCBs, RRBs and District cooperative banks through their own Data Centres. Some of the major Urban Cooperative banks have also been providing IT support to the small Urban cooperative banks and having collaborative arrangements among themselves for sharing common IT infrastructures such as Data Centres and ATM networks. The working group requested six cooperative banks located in and around Mumbai Region and two leading software companies regarding IT support services provided by them to the UCBs. The solution providers were also requested to share their experience and suggestions on how IT support extended to small size UCBs. 5.1 IT Solutions provided by the Urban Cooperative Banks: The responses from six UCBs in Maharashtra region, who shared information with their IT support services, are tabulated in the annexure in this chapter. The banks have indicated their collaboration and support as under: Consultancy and training services:
Services such as Infrastructure as a Service:
Services such as Software as a Service / ASP:
Product Offerings: Developing and selling the products which are used in the banks for :
Access to Electronic Payment system
It was observed that these banks which were based in western Maharashtra were providing solutions and services to urban banks located in states like J &K, West Bengal, Gujarat, Madhya Pradesh, Tamil Nadu, Karnataka, etc. Similarly the Software Solutions providers had then providing support to banks located across India. Thus, the geographical proximity or separation was not a either constraining or contributory factor and cloud services were geography neutral due to availability of good telecommunication network. 5.2 IT Solutions presently provided by Solution providers ASP model provided by Software Developers Cloud type services are provided by many software companies. Full details could not be ascertained but as per the responses received one of the solution providers has been providing core banking solution to around 53 banks and last year it had around 5800 branches using its ASP model. The software company has been pursuing with many more banks and has been awarded contract for ASP model for about 70 Cooperative banks in Rural credit structure. During the discussion it was informed that two major software companies in India were partners in this regard and this would be extended across India. 5.2.1 Cloud Services: The cloud model of the company comprises services which can be classified as IaaS and as SaaS. These include shared hardware and software, data centre and DR site, network services, Data backup and replication, etc.
5.2.2 Cloud security features : The security features mentioned by the cloud providers are :
5.2.3 Technical capabilities: The Cloud like service provider has a dedicated project team comprising project managers and other IT professionals to ensure monitoring of SLA. In terms of geographic spread as well as banking business volume handled by cloud solutions, the cloud provider has significantly large share and it has provided link to ATM networks for its cloud solutions. Wherever the leased line telecom network is not available, access is provided over satellite network. Thus the service provider can provide facilities even to executors. 5.3 Initiatives taken by Industry Association - NAFCUB: The NAFCUB which is an Industry association of UCBs has identified CBS six vendors all over the country through a bidding process. The NAFCUB has approved ASP model for Core banking for UCBs at a monthly rental of Rs 12,900 per branch per month. NAFCUB has stated that about 350 banks have migrated to CBS so far. 5.4 Constraints faced by small UCBs in IT adoption – views of solution providers : The UCB sector is highly heterogeneous with around 42% of UCBs being unit banks, about 13 % having 2 branches, and about 20 % having 3 to 5 branches. Only 25 % of the UCBs have more than 5 branches. In view of their small size and geographical locations, small UCBs face issues of financial affordability, lack of IT awareness, technical as well as vendor management skill, procedural guidelines, language barrier, etc. A few of the IT related issues as stated by the solution providers are as follows:
5.5 Suggestions proposed by the solution providers(UCBs and Industry): 5.4.1 Suggestions from UCB service providers: As per the feedback from leading UCBs, the UCBs will derive multiple benefits from business and technological perspective, if they go for the cloud based solution (SaaS / ASP model) for banking related applications, CBS being one of the main application. This will ensure Technical inclusion of weak UCBs and improve process of Financial Inclusion. The benefits that will accrue to UCBs will be:
5.4.2 Views / Suggestions by the Software solution providers : One of the suggestions received was related to the consortium of UCBs and software company for cloud computing solution. The input provided by a software major mentions various cloud based banking services being provided and used in banks besides core banking as share accounting, HR and Payroll management, funds and investments, credit application processing and tracking, liquidity forecast, etc. In the opinion of the software major, infrastructure facilities such as channels like switches for ATM or IVR could also be deployed on cloud. The proposal has a cautionary suggestion which mentions a need for strong audit, clarity for roles and responsibilities of cloud provider, measurement metrics to be evolved. The suggestion also stresses need for standardisation, transparent pricing mechanism, well documented contracts, defining mechanisms to measure SLA, providing a single point of contact, etc. As regards provisioning of computing resources and management, the suggestion identifies requirements for one time provisioning, ongoing change requests, day to day monitoring and incident reporting. The software company has also discussed requirements for ensuring portability and interoperability as well as Security and privacy of data. One of the suggestions made during the discussion on cloud option was to have ffocused group to interpret NIST’s roadmap and apply it to cloud deployment for UCB segment. This group could discuss following aspects of cloud adoption.
5.4.3 Emerging ICT solutions for small Urban Cooperative banks The responses received indicate that the UCB segment already has a number of solution providers providing Cloud like solutions and telecommunication companies are providing cloud carrier services. Besides UCBs many RRB and the Cooperative Credit banks in rural credit structure also availing such computing solutions. All these solution providers have their own methodologies for identification of solutions, entering into legal contracts, ensuring data security and performance measurement as well as monitoring of SLA. However, as reflected from the suggestion received from software majors who have better understanding of the potential and limitations of the cloud solutions, there is an imperative need to address the open issues and set the standards for various aspects of cloud computing like continuation of banks, SW companies as providing Cloud like solutions to the banks for sharing infrastructures.Annexure 5.1 Responses received from the six UCBs
Chapter 6 The working group had analysed the international trends in Cloud Computing standards and developments among Urban Cooperative banking sector within India. The analysis and recommendations of the group are discussed in this chapter. 6.1 Analysis of the trends in cloud computing and its application
6.2 Recommendations The working group reviewed its terms of references in the context of the emerging trends and experiences and views of the CSP. Following recommendations are made in this context:
The Working Group would like to thank different Urban Cooperative Banks as well as the IT solution providers for their input and valuable suggestions. The group acknowledges the help received from the officers of Department of Information Technology RBI namely Shri Hemant Kumar, General Manager Shri T.K. Rajan, General Manager, Shri Sachin Shende, Deputy General Manager, and Smt Shubhangi Latey, Assistant General Manager for their analytical support and their efforts for timely completion of this report. The group would also like to thank Smt. Vibhuti Mohite for her secretarial and other support for the study. References 1. Special publication 800-146 NIST National Institute of Standards and Technology U.S. Department of Commerce http://www.nist.gov/. 2. Special publication 500-196 NIST National Institute of Standards and Technology U.S. Department of Commerce http://www.nist.gov/ 3. Special publication 500-193 NIST National Institute of Standards and Technology U.S. Department of Commerce http://www.nist.gov/index.html. 4. Special publication 800-145 NIST National Institute of Standards and Technology U.S. Department of Commerce http://csrc.nist.gov/. 5. Guiding Principles for Cloud Computing adoption and Use http://www.isaca.org 6. Control Objectives for Cloud computing http://www.isaca.org 7. ValIT Framework 2.0 http://www.isaca.org 8. Security Guidance for critical areas of focus in cloud computing version 3.0 https://cloudsecurityalliance.org 9. What is cloud computing and its background http://en.wikipedia.org/wiki/Cloud_computing 10. What is cloud computing and its background http://www.guardian.co.uk/cloud-computing/what-is-cloud-computing |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
ପେଜ୍ ଅନ୍ତିମ ଅପଡେଟ୍ ହୋଇଛି: